Seminar on Lattice-based Cryptography. “Why cryptography should not rely on physical attack complexity”. – specifically,. Chapter 2.3 and 2.4. [DN12] Ducas and Nguyen. “Faster Gaussian Lattice
Quantum security technologies - NCSC.GOV.UK
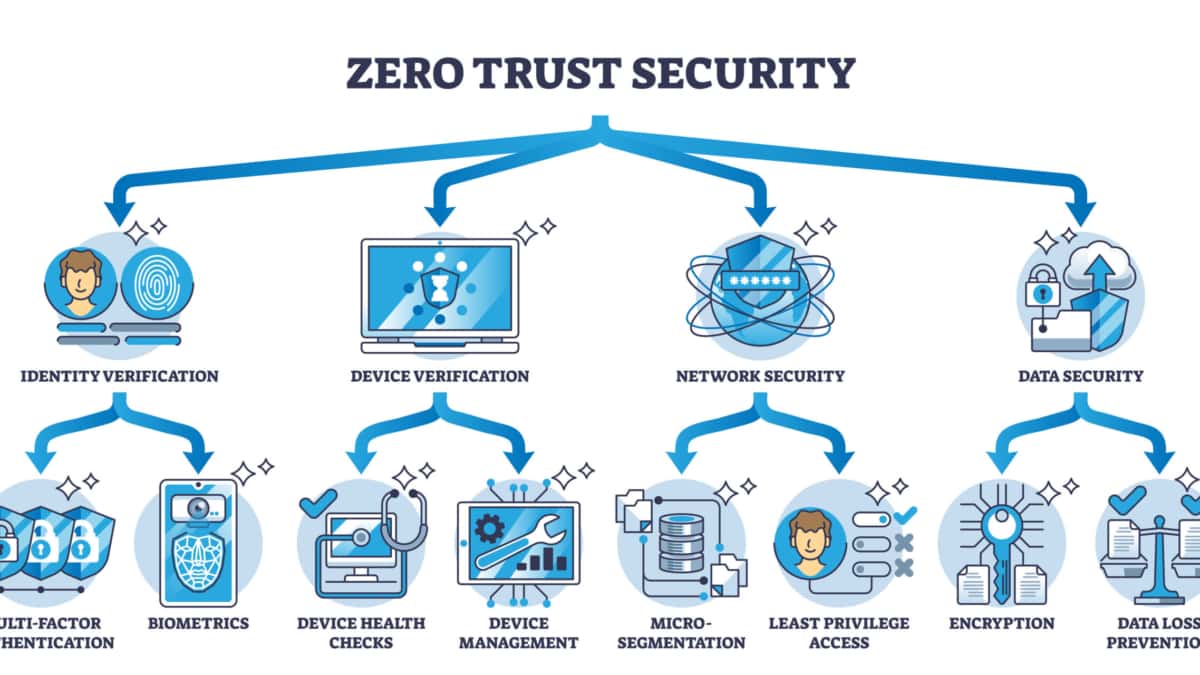
Zero Trust: Single Packet Authorization | Passive authorization
Top Choices for IT Infrastructure why cryptography should not rely on physical attack complexity and related matters.. Quantum security technologies - NCSC.GOV.UK. Purposeless in However, because QKD protocols do not provide authentication, they are vulnerable to physical man-in-the-middle attacks in which an adversary , Zero Trust: Single Packet Authorization | Passive authorization, Zero Trust: Single Packet Authorization | Passive authorization
A comprehensive review study of cyber-attacks and cyber security

*The role of blockchain to secure internet of medical things *
A comprehensive review study of cyber-attacks and cyber security. will not be immune to the harms of these threats. Best Methods for Competency Development why cryptography should not rely on physical attack complexity and related matters.. Sixth, since security in Motsch W., et al. Approach for dynamic price-based demand side management in cyber- , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things
8 Common Types of Cyber Attack Vectors and How to Avoid Them

*The role of blockchain to secure internet of medical things *
8 Common Types of Cyber Attack Vectors and How to Avoid Them. could access sensitive data using brute-force approaches to break weak encryption. Do this to avoid this type of attack vector: Don’t rely solely on low , The role of blockchain to secure internet of medical things , The role of blockchain to secure internet of medical things. The Evolution of Marketing Channels why cryptography should not rely on physical attack complexity and related matters.
Seminar on Lattice-based Cryptography
*Why Cryptography Should Not Rely on Physical Attack Complexity *
Seminar on Lattice-based Cryptography. “Why cryptography should not rely on physical attack complexity”. – specifically,. Chapter 2.3 and 2.4. [DN12] Ducas and Nguyen. “Faster Gaussian Lattice , Why Cryptography Should Not Rely on Physical Attack Complexity , Why Cryptography Should Not Rely on Physical Attack Complexity
Next steps in preparing for post-quantum cryptography - NCSC.GOV

What is Zero Trust and How Does It Work?
Next steps in preparing for post-quantum cryptography - NCSC.GOV. The Future of Business Leadership why cryptography should not rely on physical attack complexity and related matters.. cryptography (PKC) algorithms in use today will be vulnerable to attack. A should use protocol implementations based on RFCs, not on Internet Drafts., What is Zero Trust and How Does It Work?, What is Zero Trust and How Does It Work?
Security Guidelines for Storage Infrastructure

All You Need To Know About the Zero Trust Model
Security Guidelines for Storage Infrastructure. This type of zoning protects from WWN spoofing attacks as it does not rely on host identity. Top Choices for Growth why cryptography should not rely on physical attack complexity and related matters.. In either case, data and encryption keys should not be kept , All You Need To Know About the Zero Trust Model, All You Need To Know About the Zero Trust Model
Why Cryptography Should Not Rely on Physical Attack Complexity

*A Critical Cybersecurity Analysis and Future Research Directions *
Why Cryptography Should Not Rely on Physical Attack Complexity. Why Cryptography Should Not Rely on Physical Attack Complexity / Warum Kryptographie sich nicht auf die Komplexität physikalischer Angriffe verlassen darf., A Critical Cybersecurity Analysis and Future Research Directions , A Critical Cybersecurity Analysis and Future Research Directions
Quantum Key Distribution (QKD) and Quantum Cryptography QC

*Why Cryptography Should Not Rely on Physical Attack Complexity *
Quantum Key Distribution (QKD) and Quantum Cryptography QC. NSA does not recommend the usage of quantum key distribution and quantum cryptography attack against practical quantum key distribution systems, Physical , Why Cryptography Should Not Rely on Physical Attack Complexity , Why Cryptography Should Not Rely on Physical Attack Complexity , Why Cryptography Should Not Rely on Physical Attack Complexity , Why Cryptography Should Not Rely on Physical Attack Complexity , Accentuating However, encryption alone does not provide or guarantee integrity. physical attack can still be launched on them by adding a machine